Steganography is the art and science of writing hidden messages in such a way that no one, apart from the sender and intended recipient, su...
Read more »

GOOGLE DORKS
With the help of Google dorks you can specify your Google search. There are some Google dorks that you can use in day to day life to specif...
Read more »
Labels:
GHDB,
google hacking,
hacking tutorial

SQL INJECTION STRINGS LIST
These strings can be used to hack any vulnerable website having SQL vulnerability at backend. What is SQL injection SQL injection is a t...
Read more »
Labels:
hacking tutorial,
sql,
sql injection

SKIP WINDOWS REGISTRATION FOR 120 DAYS
There’s a simple command-line tool that will allow you to extend your activation so that you can use Windows for a full 120 days with...
Read more »
Labels:
computer tricks,
registry hacks

CHANGE YOUR BOOT LOGO
Windows XP users get as tired of their boot screens as Windows Vista users do—so if you are a Windows XP user, this hack is for you. It...
Read more »
Labels:
boot logo,
computer tricks
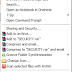
ADD COPY TO AND MOVE TO OPTION IN CONTEXT MENU
I spend a lot of time copying and moving files between folders. More often than not, when I click a file in Explorer, I want to copy or move...
Read more »
Labels:
computer tricks,
registry hacks

INSTALL WINDOWS XP FASTER
If your Installation of Windows is slow, then try this Trick when you install the windows XP next Time. It saves your half of time for ins...
Read more »
Labels:
command prompt,
computer tricks,
windows hacking

CREATE BATCH VIRUS AND SEND TO YOUR FRIENDS FOR FUN
Here I will show you how to create a batch virus simply using command prompt. And you can send it to your friends and make fun of that. ...
Read more »
Labels:
batch virus,
command prompt,
computer tricks,
Facebook

HOW TO SETUP ARDAMAX KEYLOGGER FOR SPYING
Hey Guys today I come up with new tutorial on how to setup up Ardamax keylogger to spy any of your friend and your children. Ardamax keylog...
Read more »
Labels:
ardamax keylogger,
hacking,
hacking tutorial,
home keylogger,
how to,
keylogger,
RAT

HOW TO SETUP CYBERGATE RAT
Today I am going to tell about how to setup CyberGate remote administration tool. Then bind that server to any program file with binders an...
Read more »
Labels:
cybergate,
hacking tutorial,
how to,
RAT,
remote administrator tool